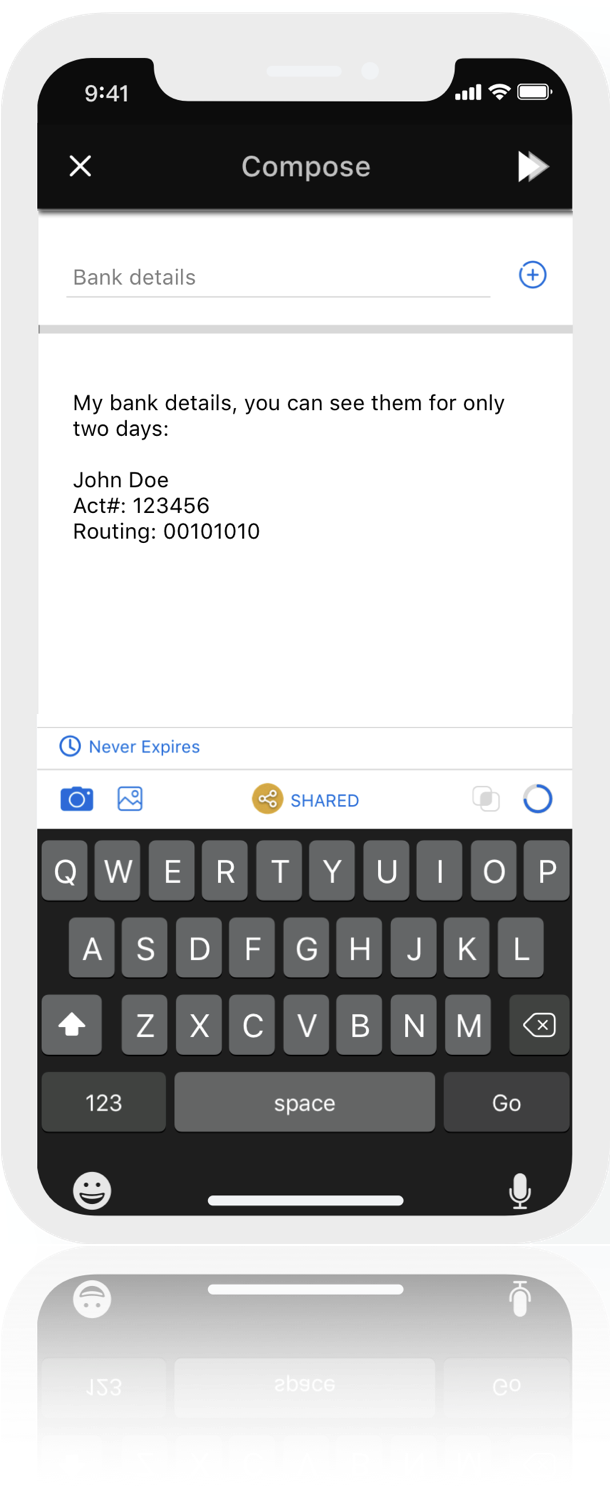
An additional layer of defense even if email accounts are compromised
Take the pressure off hacked email accounts for critical processes such as password resets. Even if your email is compromised, you are not.
How it works
In the event of your email account being compromised, hackers cannot manipulate Cyphlens images
You can use encrypted images to conduct business without worrying about whether email accounts have been compromised.
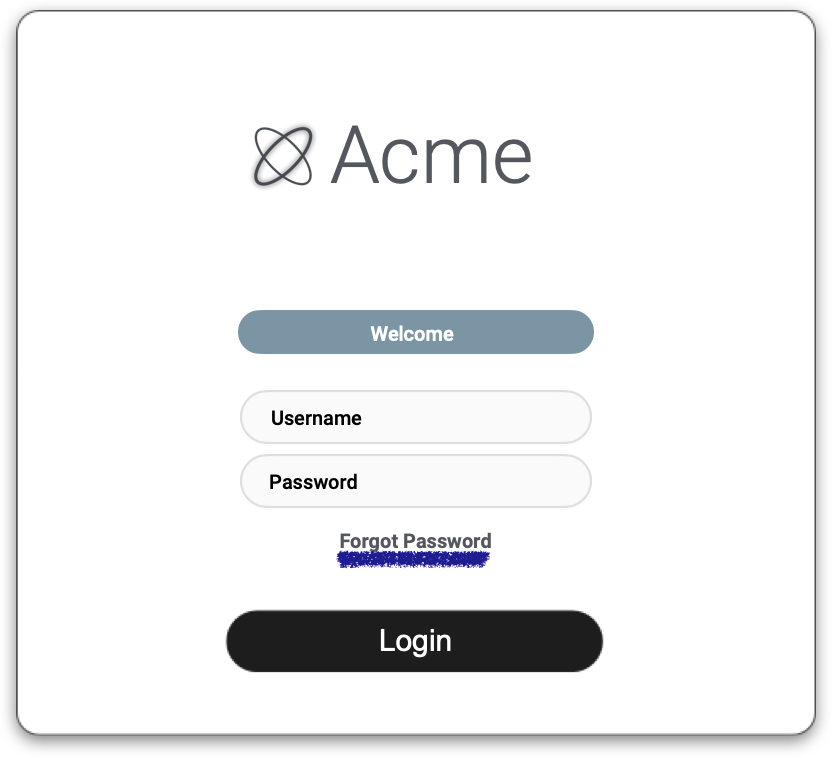
1. Request password reset
The user requests a password reset or follows the forgot password flow on a website.
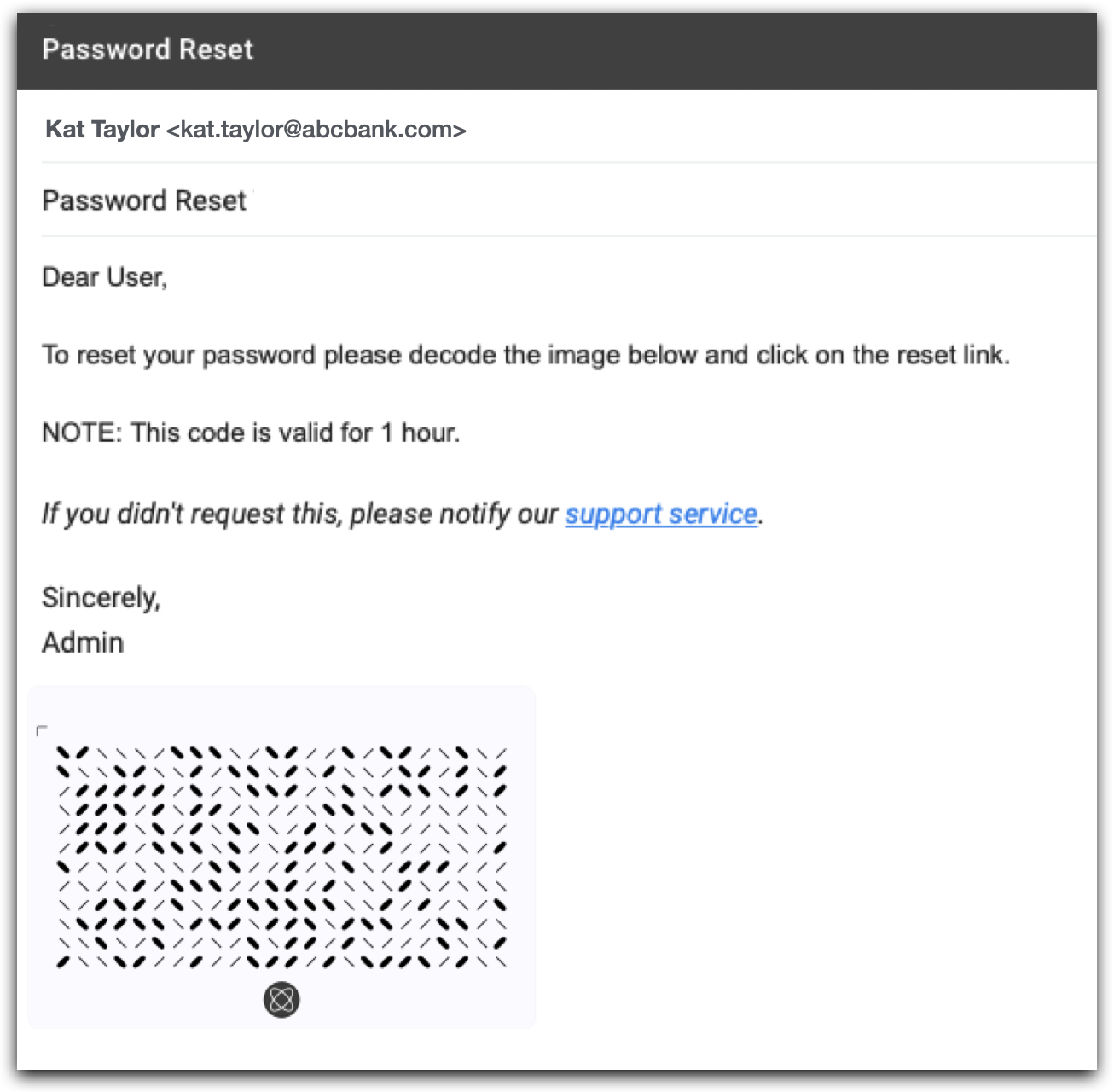
2. Receive encrypted reset link
The website creates an encrypted image of the password reset link and sends it to the user via email.

3. Decrypt link
The user decrypts the encrypted image in the email and clicks on the password reset link.
4. Password is reset
The user follows the usual flow for password reset from their mobile device.
Unique user experience
Turn your mobile camera into a powerful decryption device
With Cyphlens, your mobile camera takes on a new level of functionality. It acts as your personal decryption device, giving you access to content that only you can see, review, and approve.

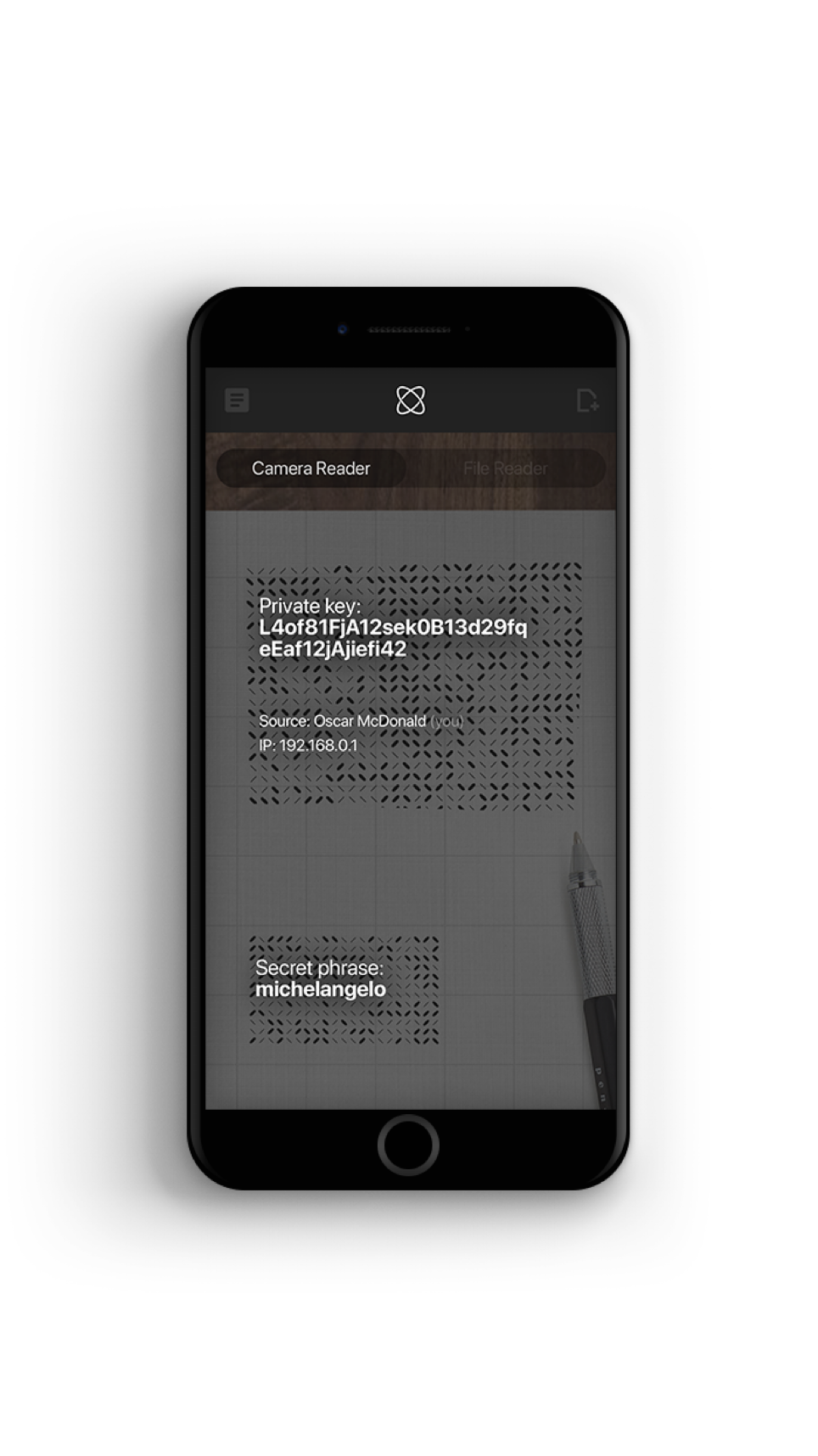
From point-to-shoot to point-to-decrypt
Point-to-Decrypt is a familiar and frictionless user experience
Cyphlens makes it as simple as just pointing your mobile camera at the encrypted content to validate and access your information, if authorized to do so.
Security beyond the login
We secure email workflows even when an email account is compromised
With Cyphlens, you can add another layer of defense to secure an email based process without being solely reliant on email account security.
Account compromise resilient
Even if a hacker has your email credentials or access to your vendor's email account, Cyphlens offers another layer of defense for critical internal processes.
Persistent auditable security
When using Cyphlens images, you can set time expirations and keep track of all interactions providing full auditability.
Email workflow compatibility
Cyphlens enabled processes can be extended across multiple email accounts internally and externally for added security.